Spnego Login Failed a Process Has Requested Access Updated FREE
Spnego Login Failed a Process Has Requested Access
This article describes how to enable Microsoft clients (browsers in this case), authenticated in a Windows domain, using Kerberos, to exist transparently authenticated in a Oracle WebLogic Server (Oracle WebLogic Server) domain, based on the aforementioned credentials, and without the need to type in a password again.
The purpose of this feature is to enable a client browser to access a protected resources on Oracle WebLogic Server, and to transparently provide Oracle WebLogic Server with authentication information from the Kerberos database via a SPNEGO ticket. Notation that this feature also works for Java SE clients. Oracle WebLogic Server will be able to recognize the ticket, and extract the data from it. The server will then use the data for hallmark and grant admission to the resource if the authenticated user is authorized to access it. (Kerberos is responsible for authentication only; authorization is still handled past Oracle WebLogic Server.)
Notation that although to a higher place configuration is used for this scenario, SPNEGO should work for older versions of browsers, Oracle WebLogic Server, JDK, then on.

Figure one: Machine Configuration for SPNEGO/Kerberos scenario
The following list of steps are a detailed breakdown of the cross-platform authentication blueprint shown above.
- When the logged-on user (MACHINEA) requests a resource from Oracle WebLogic Server (MACHINEB), it sends the initial HTTP Become verb.
- Oracle WebLogic Server (MACHINEB), running the SPNEGO Token Handler code, requires authentication and issues a 401 Access Denied, Www-Cosign: Negotiate response.
- The customer (Browser on MACHINEA) then requests the session ticket from the TGS/KDC (MACHINEC).
- The TGS/KDC (MACHINEC) supplies the client with the necessary Kerberos Ticket (assuming the client is authorized) wrapped in a SPNEGO Token.
- The customer re-sends the HTTP GET request + the Negotiate SPNEGO Token in an Authorization: Negotiate base64(token) header.
- Oracle WebLogic Server's SPNEGO Token Handler code accepts and processes the token through GSS API, authenticates the user and responds with the requested URL.
KDC Configuration
A Windows 2008 Server domain controller can serve as the Kerberos Key Distribution Center (KDC) server for Kerberos-based client and host systems.
Create an Account for Oracle WebLogic Server Server
In this pace, a Kerberos Principal representing Oracle WebLogic Server is created on the Active Directory. The principal name would be something like name@REALM.Proper noun, while the REALM.Proper noun is the administrative proper name of the realm. In our example, the principal name will be negotiatetestserver@SECURITYQA.COM. The machine hosting Oracle WebLogic Server doesn't have to exist part of SECURITYQA.com domain. In this case it's part of OTHERDOM.DOM domain. The account type should exist "User", not a "Reckoner" in the AD.
Create a User "negotiatetestserver" in Active Directory for Your Oracle WebLogic Server instance

Figure two: Account tab showing properties for "negotiatetestserver" user on KDC
- Launch Programs/Administrative Tools/Agile Directory Users and Computers tool.
- Right click on theUsersnode and selectNew/User. (Exercise not selectMachine.)
- Type in the user "negotiatetestserver" in the "Total Proper name" field and in the "Logon Name" field.
- ClickNext, and enter a password (and of course, memorize it)
- Verify that none of the countersign options are checked. ClickAdjacent.
- ClickFinish.
Configure Your User to Comply with the Kerberos Protocol
- Locate your newly created user in the Users tree in the left hand pane and double click it.
- On the "Business relationship" tab for user "negotiatestserver",
- For AES128-SHA1 null strength, make certain This business relationship supports AES 128 scrap encryption is checked; all others (except password never expires) are unchecked.
- For AES256-SHA1 zippo strength, make sure This account supports AES 256 bit encryption is checked; all others (except password never expires) are unchecked.
- For RC4-HMAC-NT cipher strength, make sure all options (except password never expires) are unchecked.
- For DES-CBC-CRC zilch strength, make certain Utilize Kerberos DES encryption types for this account and make sure all options (except password never expires) are unchecked.
- Click OK.
Ascertain a Service Principal Name and Create a Keytab for the Service
An SPN (Service Principal Name) is a unique name that identifies an instance of a service and is associated with the logon account nether which the service instance runs. The SPN is used in the procedure of mutual hallmark between the client and the server hosting a detail service. The client finds a estimator business relationship based on the SPN of the service to which it is trying to connect.
The ktpass command-line tool enables an ambassador to configure a non-Windows Server Kerberos service as a security principal in the Windows Server Active Directory. Ktpass configures the server principal name for the service in Active Directory and generates an MIT-style Kerberos "keytab" file containing the shared secret key of the service. The tool allows UNIX-based services that back up Kerberos hallmark to utilise the interoperability features provided by the Windows Server Kerberos KDC service.
Use the following command to configure SPN (for AES128 cipher forcefulness) and generate keytab file:
C:\Users\bt>ktpass -out negotiatetestserver_keytab -princ negotiatetestserver@SECURITYQA.COM -mapUser negotiatetestserver -kvno 0 -crypto AES128-SHA1 -pass -p type KRB5_NT_PRINCIPAL Save generated keytab file (negotiatetestserver_keytab) in a secure location, and export it to the domain directory of your Oracle WebLogic Server. (In our case, we will transfer this file to MachineB.) This file is reference by a JAAS (Java Authentication and Authorization Service) configuration file explained later.
Oracle WebLogic Server Server Configuration
The important requirements for the configuration of this server are:
- The server has to be represented in the Kerberos realm via a Kerberos principal (which nosotros defined in the previous department).
- The server needs to be able to access the KDC.
- The Oracle WebLogic Server procedure needs to have access to the credentials of its account in Kerberos.
- Oracle WebLogic Server must be configured to recognize a spnego token in a asking.
Create JAAS Login File
JAAS allows dynamic configuration of login modules. We need to specify a JAAS configuration file that specifies the login modules to use.
Create a file namedkrb5Login.confin the Oracle WebLogic Server domain directory with the post-obit contents:
For Oracle WebLogic Server using Oracle JDK:
com.sun.security.jgss.initiate { com.sun.security.auth.module.Krb5LoginModule required master="negotiatetestserver@SECURITYQA.COM" useKeyTab=true keyTab=negotiatetestserver_keytab storeKey=true debug=true; }; com.sun.security.jgss.krb5.accept { com.sun.security.auth.module.Krb5LoginModule required principal="negotiatetestserver@SECURITYQA.COM" useKeyTab=truthful keyTab=negotiatetestserver_keytab storeKey=true debug=true; }; For Oracle WebLogic Server using IBM JDK:
com.ibm.security.jgss.initiate { com.ibm.security.auth.module.Krb5LoginModule required main="negotiatetestserver@SECURITYQA.COM" useKeyTab=true keyTab=negotiatetestserver_keytab storeKey=true debug=true; }; com.ibm.security.jgss.accept { com.ibm.security.auth.module.Krb5LoginModule required chief="negotiatetestserver@SECURITYQA.COM" useKeyTab=true keyTab=negotiatetestserver_keytab storeKey=true debug=true; }; Using Startup Arguments for Kerberos Authentication with Oracle WebLogic Server
This assumes you lot have transferred the keytab file "negotiatetestserver_keytab" generated in pace ii to your domain directory on Oracle WebLogic Server. If Oracle WebLogic Server is using Oracle JDK, specify following options in the Oracle WebLogic Server java command line:
-Dcom.ibm.security.jgss.debug=all -Djava.security.krb5.realm=SECURITYQA.COM -Djava.security.krb5.kdc=MACHINEC -Djava.security.auth.login.config= krb5Login.conf -Djavax.security.auth.useSubjectCredsOnly=false Configure Identity Assertion provider
WebLogic Server includes a security provider, the Negotiate Identity Exclamation provider, to support single sign-on (SSO) with Microsoft clients. This identity exclamation provider decodes Simple and Protected Negotiate (SPNEGO) tokens to obtain Kerberos tokens, validates the Kerberos tokens, and maps Kerberos tokens to WebLogic users. You need to configure a Negotiate Identity Assertion provider in your WebLogic security realm in social club to enable SSO with Microsoft clients. See Configuring a Negotiate Identity Assertion Provider .
Install Java Cryptography Extension (JCE) Unlimited Forcefulness Jurisdiction Policy Files
(This step is applicative only if you program to use AES256-SHA1 nix strength. Skip this step for all other cypher strengths). You need to download and install this bundle which provides "unlimited force" policy files which incorporate no restrictions on cryptographic strengths.
- For Oracle JDK six: Download Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files vi here.
- For Oracle JDK 7: Download Coffee Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 7 hither. Overwrite 2 jar files under "
/jre/lib/security" directory with 2 jar files inside downloaded zip file. - For IBM JDK 6 and to a higher place: Download Coffee Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files seven hither and follow installation instructions
Ascertain Security Constraint in Web Application
In order for hallmark to accept place, the resource (JSP or Servlet) existence accessed must be protected, and for the web application to participate in Single Sign On with the customer.
Here's the servlet code used in our case (SimpleTestServlet.coffee):
packet wlstest.functional.security.negotiate.servlet; import java.io.IOException; import java.io.PrintWriter; import java.util.Enumeration; import javax.servlet.ServletException; import javax.servlet.http.HttpServlet; import javax.servlet.http.HttpServletRequest; import javax.servlet.http.HttpServletResponse; import javax.servlet.http.HttpUtils; public class SimpleTestServlet extends HttpServlet { public void service(HttpServletRequest req, HttpServletResponse res) throws ServletException, IOException { res.setContentType("text/html"); PrintWriter out = res.getWriter(); out.println(" "); out.println(" Simple Test Servlet "); out.println(" "); out.println(" Requested URL:
"); out.println(" "); out.println(HttpUtils.getRequestURL(req).toString()); out.println(" "); Enumeration theEnum = getServletConfig().getInitParameterNames(); if (theEnum != null) { boolean get-go = true; while (theEnum.hasMoreElements()) { if (outset) { out.println(" Init Parameters
"); out.println(" "); first = false; } String param = (String) theEnum.nextElement(); out.println(" "+param+": "+getInitParameter(param)); } out.println(" "); } out.println(" Asking data:
"); out.println(" "); print(out, "Request method", req.getMethod()); impress(out, "Asking URI", req.getRequestURI()); print(out, "Asking protocol", req.getProtocol()); print(out, "Servlet path", req.getServletPath()); print(out, "Path info", req.getPathInfo()); print(out, "Path translated", req.getPathTranslated()); print(out, "Query cord", req.getQueryString()); impress(out, "Content length", req.getContentLength()); impress(out, "Content blazon", req.getContentType()); print(out, "Server name", req.getServerName()); print(out, "Server port", req.getServerPort()); print(out, "Remote user", req.getRemoteUser()); impress(out, "Remote address", req.getRemoteAddr()); impress(out, "Remote host", req.getRemoteHost()); print(out, "Scheme", req.getScheme()); impress(out, "Authorisation scheme", req.getAuthType()); impress(out, "Request scheme", req.getScheme()); out.println(" "); Enumeration e = req.getHeaderNames(); if (e.hasMoreElements()) { out.println(" Request headers:
"); out.println(" "); while (e.hasMoreElements()) { String proper noun = (Cord)e.nextElement(); out.println(" " + name + ": " + req.getHeader(name)); } out.println(" "); } e = req.getParameterNames(); if (e.hasMoreElements()) { out.println(" Servlet parameters (Single Value style):
"); out.println(" "); while (eastward.hasMoreElements()) { String proper noun = (String)e.nextElement(); out.println(" " + name + " = " + req.getParameter(name)); } out.println(" "); } due east = req.getParameterNames(); if (e.hasMoreElements()) { out.println(" Servlet parameters (Multiple Value fashion):
"); out.println(" "); while (e.hasMoreElements()) { String name = (String)e.nextElement(); String vals[] = (String []) req.getParameterValues(proper noun); if (vals != null) { out.impress(" " + name + " = "); out.println(vals[0]); for (int i = 1; i"); } out.println(" "); } out.println(" Asking Attributes:
"); e = req.getAttributeNames(); if (e.hasMoreElements()) { out.println(" "); while (e.hasMoreElements()) { String proper name = (String)e.nextElement(); Object o = req.getAttribute(name); if (o == null) continue; out.println(" " + name + ": type=" + o.getClass().getName() + " str='" + o.toString() + "'"); } out.println(" "); } out.println(" "); } private void print (PrintWriter out, String proper noun, String value) { out.print(" " + proper name + ": "); out.println(value == naught ? "<none>" : value); } private void print (PrintWriter out, String name, int value) { out.print(" " + proper name + ": "); if (value == -1) out.println("<none>"); else out.println(value); } } The spider web.xml file looks similar this:
Simple Examination Servlet (Basic Auth) BasicAuthSimpleTestServlet /* / POST Become negotiateAdminRole no description NONE negotiateAdminRole BASIC default BasicAuthSimpleTestServlet wlstest.functional.security.negotiate.servlet.SimpleTestServlet /BasicAuthSimpleTestServlet BasicAuthSimpleTestServlet / The role negotiateAdminRole is defined in weblogic.xml, equally follows:
negotiateAdminRole negotiateAdmin Administrators Client Configuration
For Unmarried Sign On to occur y'all will need an authenticated Microsoft client, belonging to the domain controlled by your realm, and requesting access to the Oracle WebLogic Server service
Configuring Internet Explorer Browser
To configure an Net Explorer browser to use Windows authentication, follow these procedures in Internet Explorer.
Configure Local Intranet Domains
- In Internet Explorer, select Tools > Internet Options.
- Select the Security tab.

Figure 3: Local Intranet Dialog Box for Internet Explorer
- Select Local intranet and click Sites.
- In the Local intranet popup, ensure that the Include all sites that bypass the proxy server and Include all local (intranet) sites not listed in other zones options are checked.
- Click Advanced.
- In the Local intranet (Avant-garde) dialog box, add all relative domain names that will be used for Oracle WebLogic Server instances participating in the SSO configuration (for instance, myhost.instance.com) and click OK.

Figure five: Configure Intranet Authentication
Configure Intranet Authentication
- Select Tools > Internet Options.
- Select the Security tab.
- Select Local intranet and click Custom Level... .
- In the Security Settings dialog box, scroll to the User Authentication department.
- Select Automatic logon simply in Intranet zone. This selection prevents users from having to re-enter logon credentials, which is a key slice to this solution.
- Click OK.
Verify Proxy Settings
If you accept a proxy server enabled:
- Select Tools > Net Options.
- Select the Connections tab and click LAN Settings.
- Verify that the proxy server address and port number are correct.
- Click Advanced.
- In the Proxy Settings dialog box, ensure that all desired domain names are entered in the Exceptions field.
- Click OK to close the Proxy Settings dialog box.
Configuring Mozilla Firefox Browser
To configure a Firefox browser to use Windows Integrated authentication, complete the post-obit steps:
- Start Firefox.
- Enter most:config in the Location Bar.
- Enter the filter string network.negotiate.
- Set the preferences as shown in Effigy below:

Figure half-dozen: Preferences Required in Firefox for Windows Integrated Authentication
Configuring Google Chrome Browser
No special configuration needed for Chrome Browser.
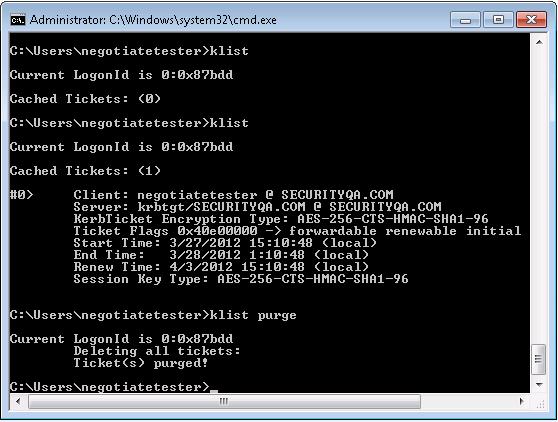
Figure vii: Using klist to view and purge tickets
Verifying Configuration
- Login to MachineA (Browser Customer) as user "SECURITYQA.COM\
- Open command prompt and run 'klist purge'. This is to purge any existing tickets.
- Open browser and access url of the spider web awarding. In this case, we are accessing a servlet which provides basic HTTP header data:
Here are typical exceptions you might run across during SPNEGO setup along with solutions:
SSO Cross-platform authentication is accomplished by emulating the negotiate behavior of native Windows-to-Windows authentication services that use the Kerberos protocol. In order for cross-platform authentication to work, Oracle WebLogic Server can exist used to parse SPNEGO tokens in society to extract Kerberos tokens which are then used for authentication thus providing transparent authentication to the cease user.
Spnego Login Failed a Process Has Requested Access
DOWNLOAD HERE
Source: https://www.oracle.com/technical-resources/articles/middleware/idm-weblogic-sso-kerberos.html
Posted by: audreyselit2001.blogspot.com


Comments
Post a Comment